Concept
CYRENE aims to enhance the security, privacy, resilience, accountability and trustworthiness of Supply Chains through the provision of a novel and dynamic Conformity Assessment Process that evaluates the security and resilience of supply chain services, the interconnected IT infrastructures composing these services and the individual devices that support the operations of the SCs. In particular, the proposed CAP will support, at different levels, SCs security officers and operators to recognize, identify, model, and dynamically analyse cyber risks. Moreover, it will support forecasting, treatment and response to advanced persistent threats and handle daily cyber-security and privacy risks, incidents and data breaches.
In doing so, CYRENE’s Conformity Assessment Process will support different types of assessment including:
- Self assessment, where organisations self assess the security, resiliency and privacy of their supply chain
- Third-party assessment, where an independent party performs the assessment, and self-attestation where the manufacturer or service provider makes a public statement.
Moreover, CYRENE aims to create certification schemes to support security and resilience of SCs through the following schemes:
- Security Certification Scheme for Supply Chain (e.g. risk assessment tool and process);
- ICT Security Certification Scheme for ICT-based or ICT-interconnected Supply Chain;
- ICT Security Certification Scheme for SCs’ (e.g. Maritime, Transport or Manufacturing) IoT devices and ICT systems that should differ from traditional IoT and systems as more stress should be put on data protection and privacy issues.
As such, CYRENE establishes new scientific foundation and radical shift in assessing and reducing security risks and incidents, cascading effects of threats, and propagated vulnerabilities, addressing the complexity of underlying interconnected CIIs, supply chain services, applications and cyber assets. In doing so, the project will bring together and advance the state of the art in various research fields including security engineering (e.g., forecasting, detection and prevention of supply chain propagated vulnerabilities), supply chain certification and audit (e.g., conformity assessment and certification schemas) and privacy engineering (e.g., privacy assessment of SCs).
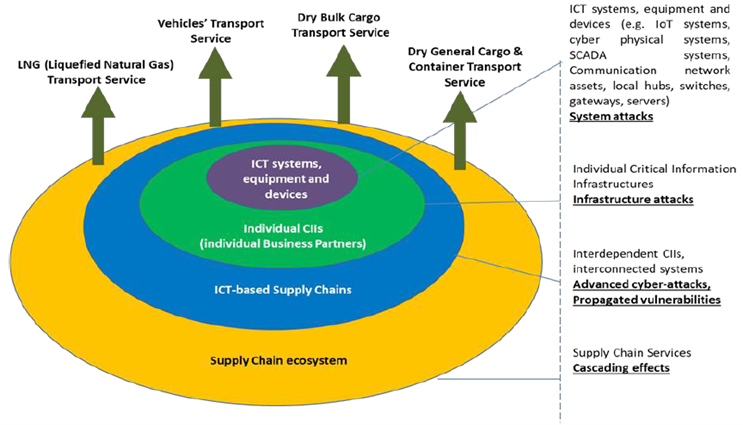
ICT-based SCs can be represented as being composed by four circles of consideration. The first inner circle, our starting point, includes all the ICT systems, equipment and devices (e.g., IoT systems, cyber physical systems, SCADA systems, Communication network assets, local hubs, switches, gateways, servers) used by the business partners and support the operation of the SCs. The second circle encapsulates the previous one and incorporates the individual Critical Information Infrastructures (CIIs) operated by the individual Business Partners involved in the SCs. The third circle encloses the two previous ones and represents the Interdependent CIIs composing the ICT-empowered SCs services. Finally, the fourth and outer circle contains all the above circles complemented with the Business Perspective of the SCs such as processes information exchange, business logic, etc. The above mentioned four circles have been identified and distinguished based on the homogeneity of characteristics (safety, technical requirements, architectures etc.) identified in each one of them.
Despite the fact that these areas have their own unique characteristics, they are not independent from each other. Inner circles can be seen as the building blocks of the external ones (“onion structure”), meaning that the security of the external circles is directly affected by the inner ones. Thus, the security and the resilience of the interdependent CIIs and the SCs’ Services (SCSs), is directly affected by the security of the individual CIIs (individual Business Partners) that compose it. However, it should be noted that the overall system is not secured by simply securing its “building blocks”. There are interdependences between the different layers that have their own specificities and require cross layer coordination. Conversely, exploring the development of a secure system out of potentially insecure components is also of interest. This can be accomplished through adopting specific measures (soft and hard security controls) like the following:
Organisational measures: Put in place and implement an effective security policy; Carry out security a risk assessment regularly; Ensure appropriate business continuity and disaster recovery plans; Establish a secure development life cycle’ Develop a full end-of-life strategy; Offer effective and secure patch management; Use proven solutions, i.e., well known communications protocols and cryptographic algorithms; Establish procedures for security incident handling; Participate in information sharing and coordinated vulnerability disclosure; Ensure the personnel is trained in privacy and security; Cybersecurity roles and responsibilities are established; Develop policy for processing of data by a third-party; Adopt cyber supply chain risk management policies; Make broad use of recognised solutions to known issues, even when it is not mandated by legislation;
Technical measures: Meet baseline security requirements for IoT; Carry out a risk assessment regarding the specific application area and complete it with suitable mitigation measures; The use of recognised solutions to known issues, even when it is not mandated by legislation; Ensure appropriate configuration of ICT systems and their segregation; Deploy cybersecurity measures to protect data at rest, in use and in motion; Apply appropriate traffic filtering; Use state-of-the-art cryptography and key storage methods; Put in place effective identity and access management; Ensure correct IT security maintenance; Develop policies for physical and environmental security.
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
