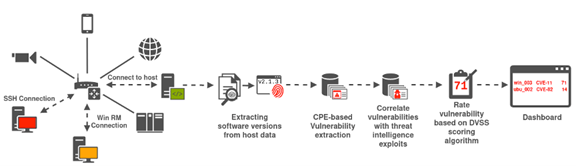
As detailed in a previous CYRENE blog post, in the context of the CYRENE project, we focus on certain cybersecurity aspects associated with the Supply Chains (SC) among which is the supply chain vulnerability assessment. The task of detecting, identifying, and measuring the vulnerabilities located in the interconnected ICT components of SC services and systems is executed by the Dynamic Vulnerability Assessment Layer (DVAL) of the CYRENE platform. At its core, DVAL dynamically assesses the supply chain’s IT infrastructure to discover vulnerable software. This is done through DVAL’s Active Detection Component (ADC). This component periodically scans the network for vulnerabilities using a 6-step process as depicted in the Figure 1.
In more details, the ADC first connects to each host configured by the system administrator. This is done via SSH or WinRM. The system administrator is advised to configure a dedicated ADC user for each host with the minimal access required by the ADC. The ADC then uses the SSH or WinRM connection to extract the host’s OS and software versions as well as the active services. The software extraction is OS-specific but often involves the use of a software package manager such as the dpkg or the RPM package managers.
Once the raw software version indicators are extracted, these indicators are processed and compared with the Common Vulnerabilities and Exposures (CVE) of the National Vulnerability Database (NVD). The ADC also labels imperfect matches meaning that its verbosity can be adjusted. Increasing the verbosity of the vulnerability matching, of course, comes with an increased risk of false positives.
The detected vulnerabilities are then enriched with information from the threat intelligence database information. Using the Exploit Code Maturity (E) obtained via the threat intelligence database and the Common Vulnerability Scoring System (CVSS) metrics obtained from the NVD, the ADC component assigns each vulnerability an updated CVSS score. Once the vulnerability has been assigned a score, DVAL provides the security administrators with vulnerability alerts empowering them to take actions to either acquire more information on the identified vulnerabilities, or to isolate the vulnerable system(s) until a security mechanism is applied.
DVAL’s ADC component will be validated in the context of the CYRENE pilots. With the pilot trails starting soon, please stay tuned for updates and lessons learned!
So what do you think? Stay Tuned for the next part of the SU blog post series on asset criticality.
Reach out to us and share your views either by using our contact form or by following our social media accounts on Twitter and LinkedIn.
Don’t forget to subscribe to our Newsletter for regular updates!
This blog is signed by: the CLS team
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.